Agentless Segmentation, Fully Managed.Deploys in hours.
Stop Lateral Threat
Deliver segmentation compliance
Granular incident response
No hardware upgrades
Built-in NAC & DHCP
Low latency, Enterprise-friendly
Airgap ZTFWTM
The First Zero Trust Firewall
Airgap is the fastest way to get over the toughest compliance hurdle in Zero Trust: segmentation.
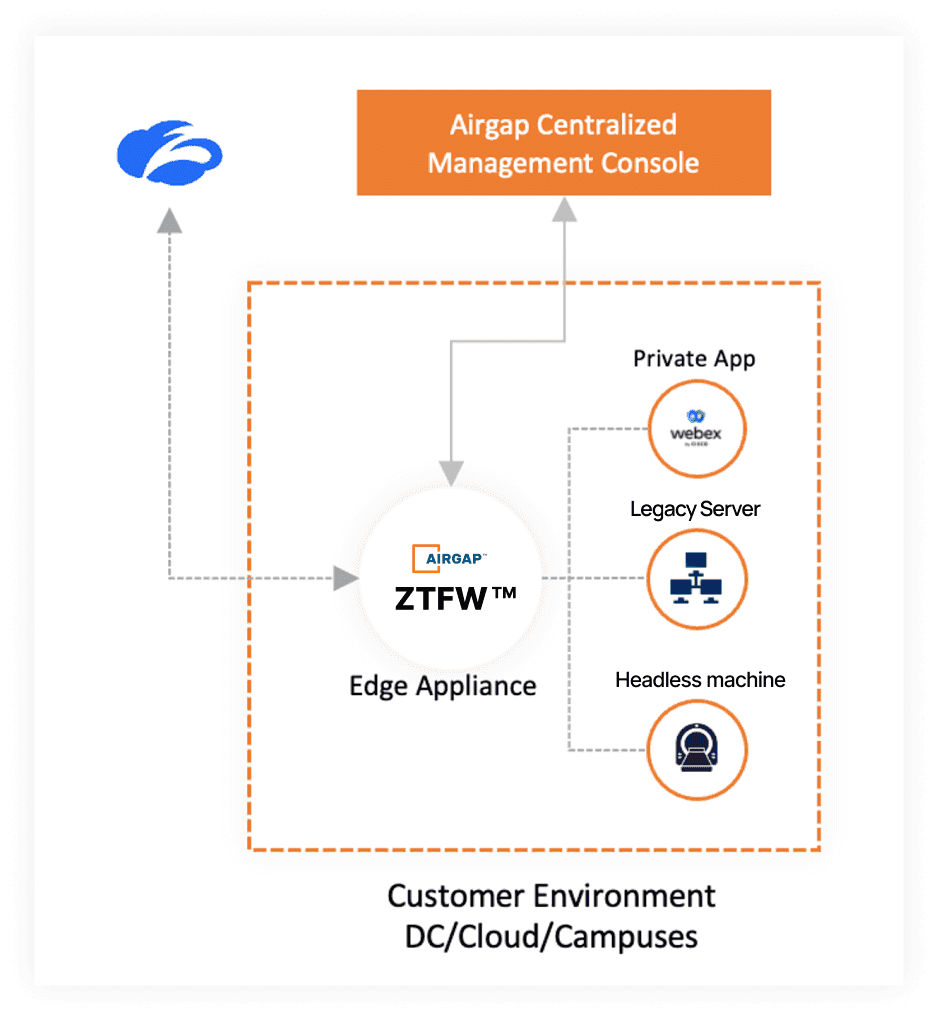
Segmentation
Say goodbye to ACLs/NAC configuration headaches
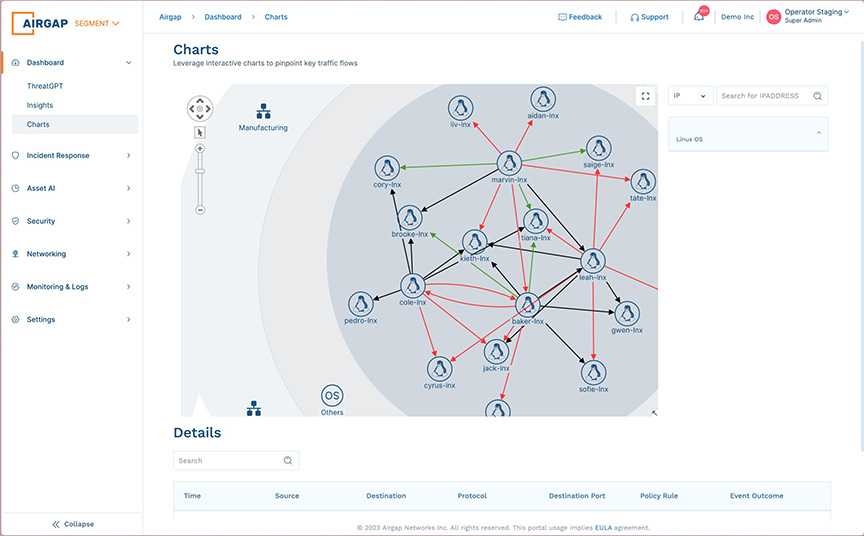
- Stop lateral threat by segmenting every endpoint
- Fully segment legacy servers, headless machines, and cloud-hosted assets
- AI/ML-driven detection
- Granular incident response
- Fully managed
- Deploys in hours
- No hardware upgrades or VLAN/IP readdressing
- Built-in NAC and DHCP
- Dozens of integrations
- Physical or virtual appliances
- Phased deployment, pay-as-you grow
- Hitless upgrades
- No open ports for attackers
- Maximized network performance
- Automated policy grouping and tagging
- Built-in visibility and discovery

Tired of Complex and Outdated ACLs/NAC?Get Airgap agentless segmentation.
Operational Simplicity & Scale
100% agentless, compliant, regularly patched, and secured. Cloud/AWS scale.
Saas/Managed Service
50% savings, fully managed, per user or enterprise annual subscription licensing.
Per-Application Customization
Custom templates to suit each app's requirements. New instances are spun up in the cloud on-demand.
Enhanced Security
SSO/MFA identity check, end-to-end encryption, lockdown from User IP to Machine IP, and authorized access only.

1:1 Demo and Tech Discussion
Skip the usual sales call.
Schedule your whiteboard technical conversation to learn why major manufacturers are switching to Airgap.
AirgapRansomware Kill Switch
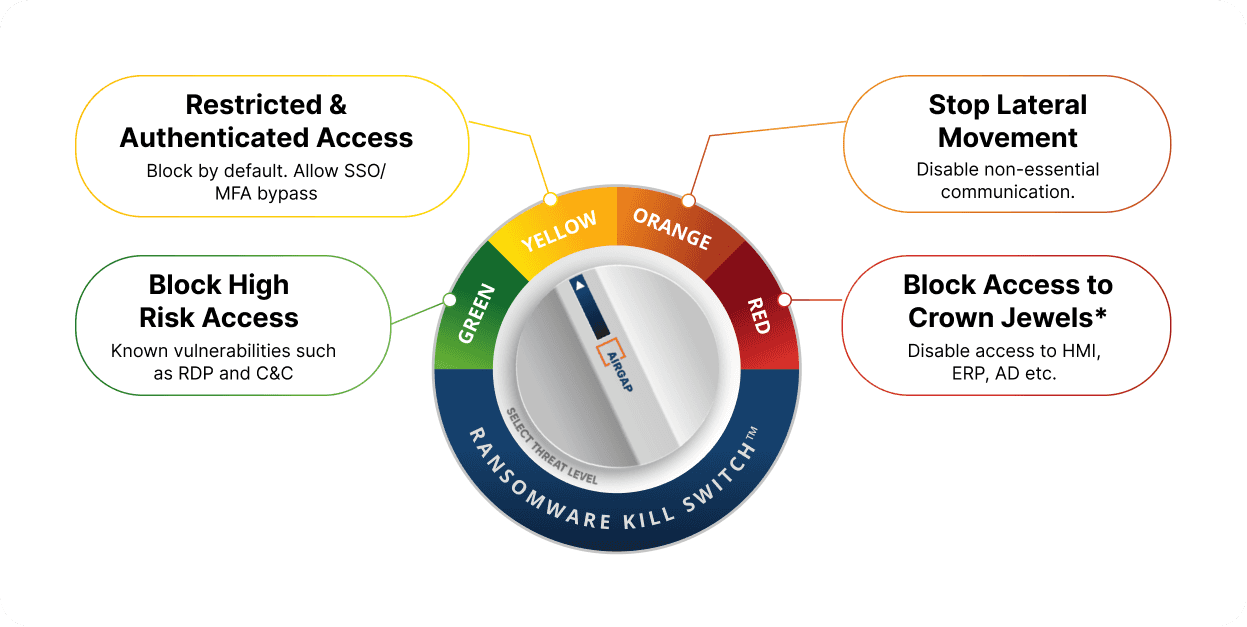
Maintain business operations even if higher network levels are compromised
Fully Compliant Segmentationin 4 simple steps
Power on airgap.io
Onboard your VLAN
Verify traffic between devices
Activate Ransomware Kill SwitchTM
You’re Protected!
Airgap Benefits
30 day trial
Fully managed SaaS
No agents
Hitless Upgrades
Audit and compliance
Deploy in hours
Pay as you grow



