Targeting gaps between Operational technology (OT), IoMT, and Industrial Control Systems (ICS) is a favorite strategy of cybercriminal gangs looking for large ransomware payouts. Processing plants, utilities, and core infrastructure are prioritized as soft targets by advanced persistent threat (APT) criminal gangs and nation-state hackers who actively target the most popular ICS and Supervisory Control and Data Acquisition (SCADA) devices.
The Cybersecurity and Infrastructure Security Agency (CISA) found that APT and cybercriminal gangs increased their real-time monitoring and surveillance of SCADA networked devices and sensors to record levels in 2022. APT and cybercriminal gangs have used advanced AI and Ml-based methods to identify unprotected sensors, endpoints, and devices to launch attacks at record levels, according to IBM's 2022 X-Force Threat Intelligence Report. In the first nine months of their study, they found an astounding 2,204% increase in automated surveillance activity by APT criminal gangs and nation-state hackers.
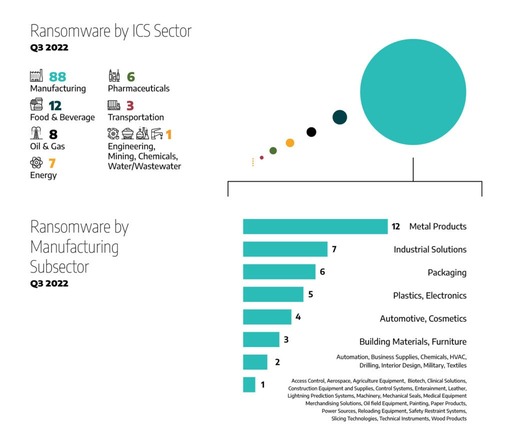
APT and cybercriminal gangs' favorite surveillance and attack targets are manufacturers and industrial solutions whose ICS and SCADA systems have no microsegmentation to kill the lateral movement. The result: industries that rely most on ICS and SCADA are attackers' favorite ransomware targets.
Why Ransomware Is The Digital Pandemic OT And IoMT Aren't Prepared For
Attacks on processing plants, core infrastructure, supply chains, and manufacturing networks that rely on ICS and SCADA systems are growing into a digital pandemic. 36% of all ransomware attacks that occurred worldwide in Q3 2022 targeted industrial organizations and infrastructures in North America first, jumping from 26% just three months before. APT and cybercriminal gangs see ICS and SCADA systems as ''the keys to the kingdom'' because each provides immediate unprotected access to manufacturers' core systems, machinery, and production assets across processing plants.
Microsegmentation is helping to stop the ransomware pandemic by eliminating lateral movement from any ransomware-infected endpoint, sensor, or device to the company network and servers. AirGap’s Zero Trust Everywhere solution is configurable to define micro-segments that support and streamline how a given business operates.
Hardening endpoints and shrinking attack surfaces using microsegmentation require granular context-based policy enforcement. Being able to ring-fence infected devices by combining microsegmentation and policy enforcement kills any chance of lateral movement by malware or ransomware on a network.
The value of micro-segmenting every sensor as an endpoint is evident based on Gartner's IoT Reference Architecture shown below, which is just as applicable to any IoMT network. When ransomware successfully penetrates edge devices and next penetrates platform systems to infect many servers quickly, enterprises have a full-scale breach in progress. Micro-segmentation consolidates edge-based endpoints, shrinking the total attack surface while immediately stopping the lateral movement of the attack payload.
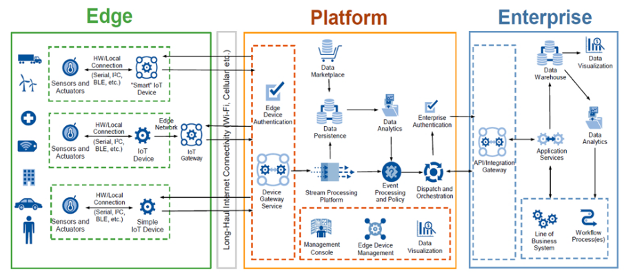
Gartner's IoT Reference Architecture provides a valuable framework for IoMT Networks. Source: Is the Purdue Model Relevant in a World of Industrial Internet of Things (IIoT) and Cloud Services? Mission Secure blog
How OT and IoMT Networks Benefit From Microsegmentation
The following are the benefits that need to be included in a business case for microsegmentation:
- Time and cost savings from improved asset discovery and identification to the sensor level across ICS and IoMT networks using micro-segmentations’ granular policy management. It’s common knowledge that up to 40% of sensor-based endpoints on ICS, SCADA, and IoMT networks aren’t discoverable on networks today. Not knowing if sensors are active and whether they’re secured often leads to inventory-based patch management. Assuming two technicians are assigned to complete a sensor audit every six months, and it takes three weeks to get done across all centralized and remote locations each time, it will take 1,250 hours in one year. At a fully burdened rate of $125 per hour, tracking down and securing sensors is approximately $156,250. Micro-segmentation would alleviate the need for periodic audits to protect sensors and endpoints.
- Not having to troubleshoot software agent and sensor updates on endpoints reduce Plant Maintenance and Production Engineering costs. The Chief Operating Officer (COO) of a plastics process manufacturing plant says that microsegmentation helps reduce the time spent up[dating endpoint agents so often by identifying every endpoint as a specific micro-segment. Plant Maintenance and Production Engineering teams waste over 670 hours yearly at a fully burdened cost per hour of $125, saving $83,750 annually.
- Eliminating the risk of a USB-based breach infiltrating the ICS and IoMT systems and spreading across corporate networks. The average cost of a single breach is $360,000, according to Ponemon’s latest study. The granular controls microsegmentation provides, along with restricting lateral access, are averting breaches today.
- Eliminating overlapping sensor and network zones, saving on hardware, software, and services licensing and maintenance costs. The data captured by micro-segmenting work areas and network zones across processing plants often uncovered duplication of networks and hardware. One COO found that interdomain controllers and security systems had expensive licensing costs at $15,400 each in ten different zones across all processing plants. Microsegmentation helped find savings of $154,000 by freeing the manufacturer from relying on interdomain control and expensive server-based licensing needed to operate them.
- Reducing the risk of fines and regulatory action by enforcing security controls consistently. Microsegmentation helps reduce compliance costs by making it easier to implement and enforce security controls required by regulatory and industry compliance standards. For example, the Health Insurance Portability and Accountability Act (HIPAA) requires healthcare organizations to maintain consistent security standards across their networks to protect the confidentiality, integrity, and availability of protected health information (PHI). Tier 1 HIPAA fines start at $10,000 per violation, with an annual maximum of $50,000, and Tier 2 is $50,000 per violation, with an annual maximum of $1.5 million. Legal costs to contest a data security violation can average $25,000 in legal fees alone.
Building A Business Case For Securing OT and IoMT Networks
The following are the microsegmentation costs that need to be included in the business case:
- Annual, often multi-year microsegmentation licensing costs. Microsegmentation providers vary in their pricing models, costs, and fees. Subscription fees of $50,000 a year are assumed for this analysis.
- Change management, implementation, and integration costs increase with IT security, Operations, and IT Service Management (ITSM) integration complexity. Expect an average price of between $40K to over $100K to integrate microsegmentation with the current security stack, including security information and event management (SIEM) systems.
The best microsegmentation business cases provide a 360-degree view of costs, benefits, and why taking action now is needed. CISOs say they've doubled down on training, change management, and ongoing support costs to ensure successful implementation.
Many include the following equation to provide an ROI estimate in their business cases. The Return on Investment (ROI) for the microsegmentation initiative is calculated as follows:
ROI on Microsegmentation (MS) = (MS Initiative Benefits – MS Initiative Costs)/MS Initiative Costs x 100.
Summary Of Microsegmentation Benefits
| Benefits of securing IT and IoMT Networks With Microsegmentation | Savings Per Year |
| Time and cost savings from improved asset discovery and identification to the sensor level across ICS and IoMT networks. | $156,250 |
| Not having to troubleshoot software agent and sensor updates on endpoints reduce Plant Maintenance and Production Engineering costs. | $83,750 |
| Eliminating the risk of a USB-based breach infiltrating the ICS and IoMT systems and spreading across corporate networks. | $360,000 |
| Eliminating network zones is no longer needed, reducing hardware, software, and services licensing and maintenance costs. | $154,000 |
| Reducing the risk of fines and regulatory action by enforcing security controls consistently. | $25,000 |
| Value Of Microsegmentation Benefits To an OT and IoMT Network in a mid-size business | $779,000 |
Based on CISOs' cost estimates of microsegmentation in a mid-size organization having the potential to save $779,000 a year and the assumption of AirGap's Zero Trust Everywhere solution costing $150,000 a year, investing in microsegmentation will yield a return of $4.19 for every dollar invested.
Bottom Line: ICS and SCADA systems are among the most porous and poorly protected networks in manufacturing, utilities, and infrastructure, making the business case for protecting them with microsegmentation. All it takes is one breached sensor or threat surface to lose millions of dollars in revenue and productivity.

