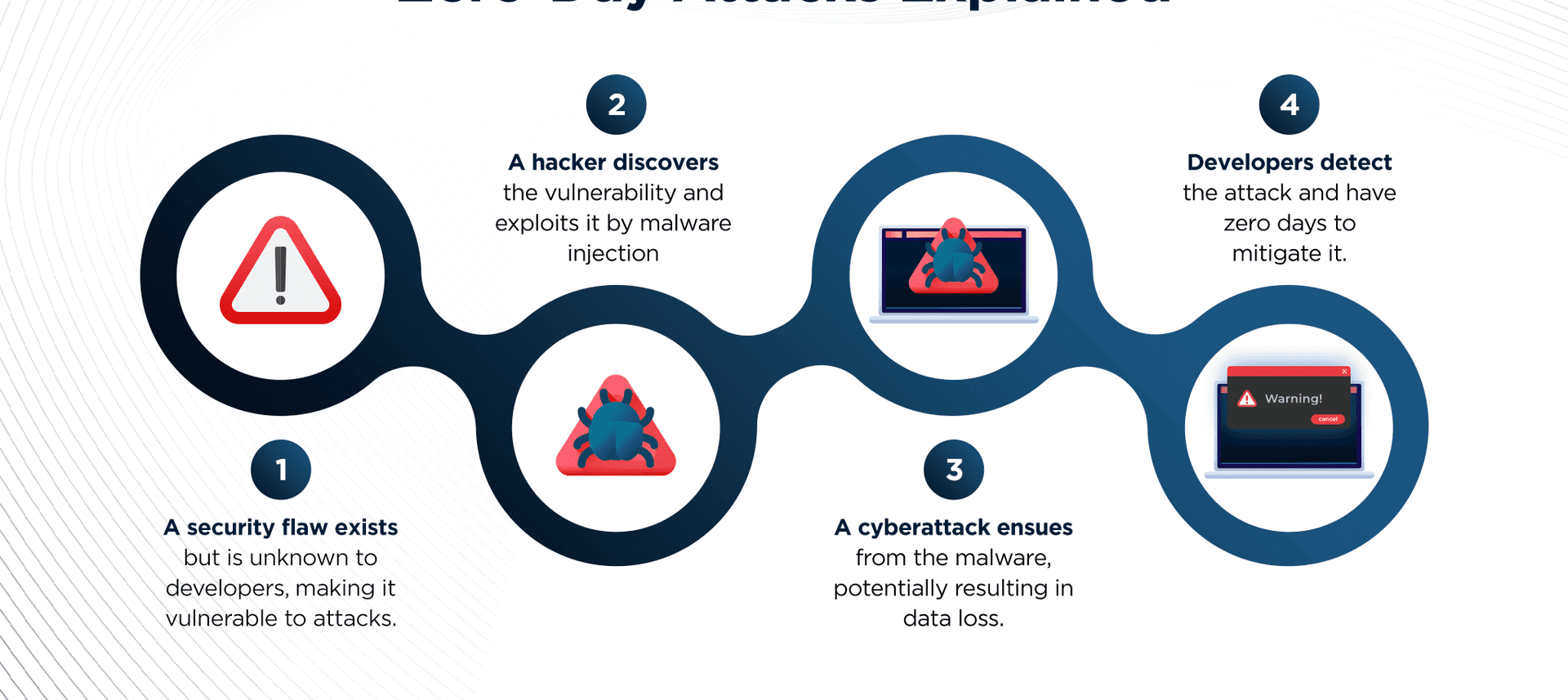
Apache Log4J, the popular Java open-source logging library used in countless applications worldwide, has been found to suffer from a significant vulnerability. A Java API for logging and tracking activities within software, log4j is estimated to have experienced 100 million compromises globally. The impact of this zero-day susceptibility registers a frightening 10 out of 10 on the Common Vulnerability Scoring System, (CVSS) and can be tracked as CVE-2021-44228.
Attackers have discovered ways to run arbitrary code on systems through Log4j. Worms can even take advantage of such flaws automatically. The attackers appear to be carrying out these attacks for a variety of malicious reasons. Some try to infect computers with crypto mining botnets while others aim to extract data from platforms such as Amazon Web Services.
What is the impact of log4j vulnerability?
The Log4j vulnerability can lead to data loss, corruption, or disclosure of sensitive data to unauthorized parties. This vulnerability can occasionally result in malicious actors gaining total control of the host and evading security controls through man-in-the-middle attacks because of improper certificate validation in the log4j SMTP appender. In specific circumstances, an attacker can gain access to an organization’s systems through remote code execution, resulting in breaches that go undetected for an extended period. Arbitrary code may be executed by the attackers from LDAP servers when message lookup substitution is enabled.
Log4j by default included a logging function known as lookups. Lookups in log4j are a mechanism to add a value to the log4j configuration. This implies that it can interpolate specified strings while logging the message.JNDI Lookups is one of the lookups offered by log4j, and it allows variables to be retrieved through Java Naming and Directory Interface, which supports LDAP. In LDAP you can store basically java serialzed objects.JNDI lookups may include a complicated java object as well as a simple string. And thus we enter the realm of arbitrary code execution. This results in an information leak and remote code execution in some environments and local code execution in all environments; remote code execution has been demonstrated on MacOS, Fedora, Arch Linux, and Alpine Linux.
If the system is equipped with Apache log4j prior to 2.17.1 or 2.3.2, it should be considered vulnerable to the Remote Code Execution vulnerabilities (CVE-2021-44228 or CVE-2021-45046) and Denial-of-service (CVE-2021-45105). In this version, message lookup has been disabled by default, but it can be bypassed with different vulnerabilities. Another feature of Log4j is the JNDI, which offers directory services to an application and may get data from a remote server using protocols like LDAP.
It is crucial to remember that merely upgrading Log4j may not be enough to fix problems if a company has previously been hacked because it contains Remote Code execution Vulnerabilities. In other words, Only just by upgrading to the most recent version of log4j will not eliminate adversary access or harmful capabilities that have already been inserted in victim situations because RCE Vulnerabilities is being already executed. To prevent exposure, Airgap advises taking a vigilant approach in examining activities in your environment, looking for indications of illegal access, and acting in accordance with incident response best practices. If you suspect you have been harmed or compromised, contact us at airgap.io to learn about remediation measures. You can also read how Airgap Zero Trust Segmentation stops zero-day exploits without resorting to implicit trust.
Airgap Ransomware Response Readiness Services(R3S) have observed that state actors are beginning to leverage these vulnerabilities in new attacks. Airgap recommends heightened vigilance in monitoring networks for abnormal activity and mobilization of response actions as necessary. Logging untrusted or user-controlled data with a vulnerable version of Log4J may lead to Remote Code Execution (RCE) against your application. Attackers can breach into systems, steal passwords and logins, extract data, and infect networks with harmful software if they dont have proper access control. Airgap Secure Asset Access (SAA) enforces the integrated Single Sign-On (SSO) before giving access to any private apps, adhering to security-first and zero trust principles.
How to prevent log4j exploits?
The best and most effective way to address this vulnerability is to upgrade log4j dependencies to the most recent version provided by Apache, log4j 2.17.0. Developer required the secure gateways to project Web, SSH and RDP based Application from credentials compromise and want to enable SSO/MFA for private applications. Airgap Secure Asset Access provides an additional security layer with MFA and SSO for any device, any user, from any location and provide multiple gateways for a set of applications and DNS for load balancing.
Airgap Zero Trust Segmentation is an agentless solution that can be deployed in minutes without third-party integration. This will make the system less dependent and less vulnerable. Zero Trust Segmentation will protect managed and unmanaged devices and permit only authorized traffic. Airgap’s Agentless Zero Trust Isolation addresses these critical security challenges, offering an optimal defense against cyberthreat propagation. Airgap’s Zero Trust Isolation prevents lateral threat propagation by isolating devices from each other if the one of the application is affected by log4j vulnerability.
A WAF (Web Application Firewall) cannot completely protect against its exploitation. Airgap Zero Trust Isolation Gateway serves as the new default gateway for the assigned VLAN and logically safeguards L2 network switched and the existing default gateway. It protects its isolated network microsegment and can restrict or limit LDAP, HTTP, and other traffic from server workloads while segregating containerized apps from internal trusted servers using Log4j.
According to many security researchers, there are always ways to exploit JNDI Injection, even with the release of new java versions where remote serialization is disabled. This exposes Log4Shell vulnerabilities for use in remote code execution, independent of the underlying JRE/JDK version. Airgap Zero Trust Isolation provides easy integration with APIs and built-in integration with Security Incident and Event Managemnt (SIEM) and Security Orchestration, Automation and Response (SOAR) technology helps coordinate, execute and monitor advanced traffic and access logs.
About Airgap Networks
Security experts know that network segmentation is the best defense against evolving cyber threats. However, available segmentation solutions require either installed agents upgrades to networking hardware with proprietary implementations. Airgap is the only vendor that offers agentless network segmentation and autonomous policy controls through a patented and innovative approach that enables isolation at every layer and down to every device. All this means malware is immediately blocked from traversing the network, even within the same VLAN or same subnet.
Additionally, a typical organization takes hours or days to detect and respond to ransomware attacks. Panicked, they often resort to draconian measures such as shutting down the entire network during a cyber event, resulting in severe operational disruption. Airgap has built a specialized Ransomware Kill Switch that surgically stops ransomware propagation with minimal operational impact.
Finally, enterprises often enable direct access to high-value assets over vulnerable protocols such as Windows RDP. Airgap’s identity-based access control provides strong zero trust safeguards as an additional layer of protection.
Airgap’s patented solution is custom-designed to reduce the enterprise attack surface and protect high-value assets in manufacturing, healthcare, retail, and critical infrastructure verticals where a compromised core operational system can bring down mission-critical processes. Airgap Agentless Security Platform is the easiest to implement and manage and it is currently deployed across many large multinational customers.
Contact Airgap at info@airgap.io and test drive modern agentless segmentation with zero trust.